Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Steps & Examples - CrowdStrike

How to Do Malware Analysis?

Malware analysis file Malicious activity
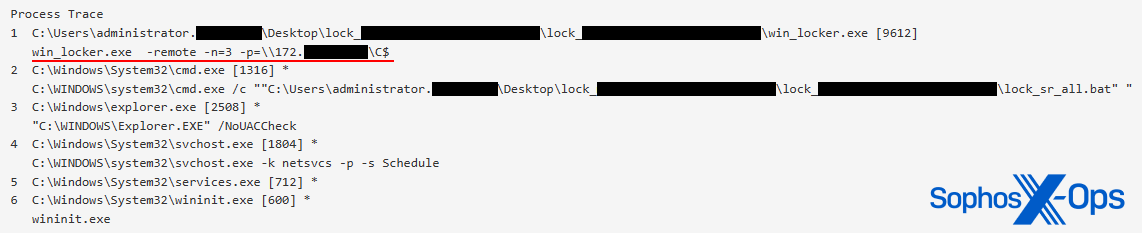
CryptoGuard: An asymmetric approach to the ransomware battle – Sophos News
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

MetaDefender Cloud Advanced threat prevention and detection
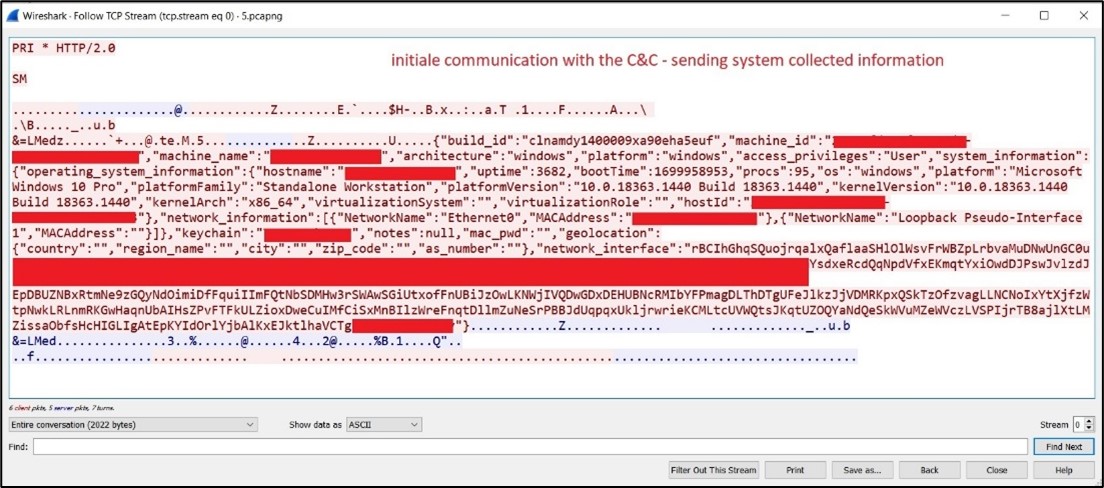
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
de
por adulto (o preço varia de acordo com o tamanho do grupo)